This post presents the experience of the Radboud University master student Tom Nijholt during an internship at Secura. Both the university and the company are partners of the INTERSECT Public Private Partnership.
Originally written by Tom Nijholt
At the end of last year I spent 3 months on a research internship as a Radboud University master student at Secura where we looked at the in-development Cybersecurity for Consumer IoT Standard (EN 303 645 [1]) from the European Telecommunications Standards Institute (ETSI). The goal of this standard is to draw a baseline of requirements for Consumer IoT products that would ensure a baseline level of cybersecurity. In the standard are 13 categories of provisions that comprises most of the vulnerability vectors IoT devices have been dealing with [2] in an attempt to mitigate cyberattacks and protect consumer privacy on IoT products.
The goal of the research was to analyse the standard and detail a set of black-box tests that can confirm that a device adheres to the requirements laid out in the standard.
The standard
We first spent some time analysing the standard and found that quite a few requirements were not all that precisely defined. For example the requirements mentions multiple times the notion of “appropriate cryptography”, but never actually defines what appropriate cryptography is. We would have liked to have the standard at least describe a minimum level of cryptography. We were able to discuss this and our other findings at an public enquiry at NEN, the dutch normalisation institute. Nonetheless, we created a first version of a list of concrete tests or guidelines
on how to confirm whether an IoT device adheres to the ETSI standard. After drafting these tests we applied them to an actual IoT device to determine usability. For the research we chose an IP camera with extensive features controlled by a smartphone application allowing us to cover nearly the entire set of tests. We quickly realised that in order to confirm with confidence that requirements were met, internal access to the device would be required. Gaining internal access to an IoT device being one of the attack vectors the ETSI standard aims to protect against.
Reverse engineering
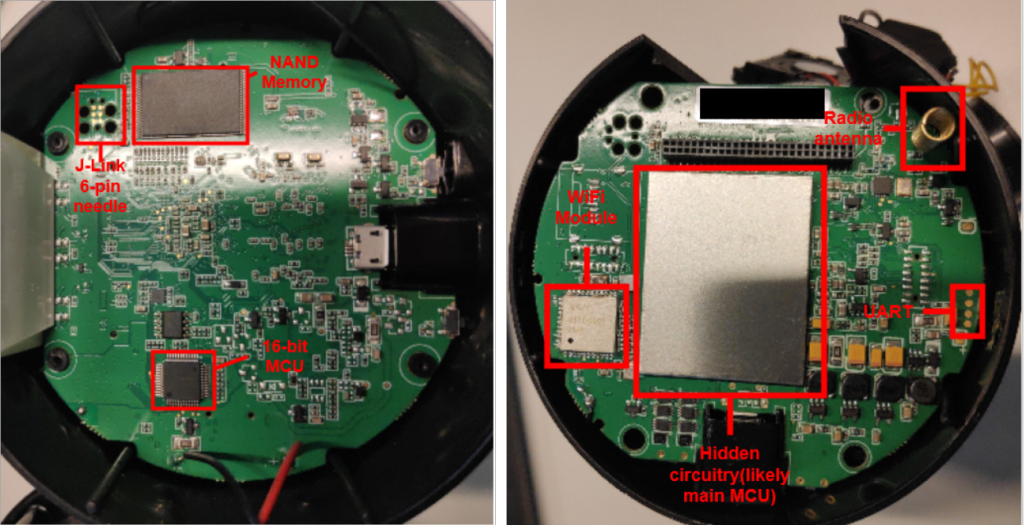
For our method of reverse engineering we followed previous research by Schwartz et al on reverse engineering full stack devices [3]. We inspected the physical device and noted several possible points of access. Our first attempt was accessing the device through the UART port. We soldered on some wires and opened up a serial connection. When powering on the IP camera we were greeted with a login prompt. Possible methods of circumventing such a login prompt are simply pressing a key during boot dropping into the bootloader, brute-forcing the login or inducing hardware faults to drop the serial connection to a privileged environment. Unfortunately we had no luck with above methods so we went on to a more drastic method namely dumping the contents of the NAND flash memory unit. In our inspection process we identified a NAND flash memory unit. Being the main storage unit of the IP camera it could contain all the data we needed to confirm adherence to the ETSI standard or perhaps to discover hardcoded passwords that would enable gaining interactive access to the device. We found a solution to dump all of the data found on the device with dumpflash [4]. We desoldered the NAND flash unit from the main PCB and connected it to a pc using a PCB and a FTDI 2232H mini and proceeded to dump all the contents.
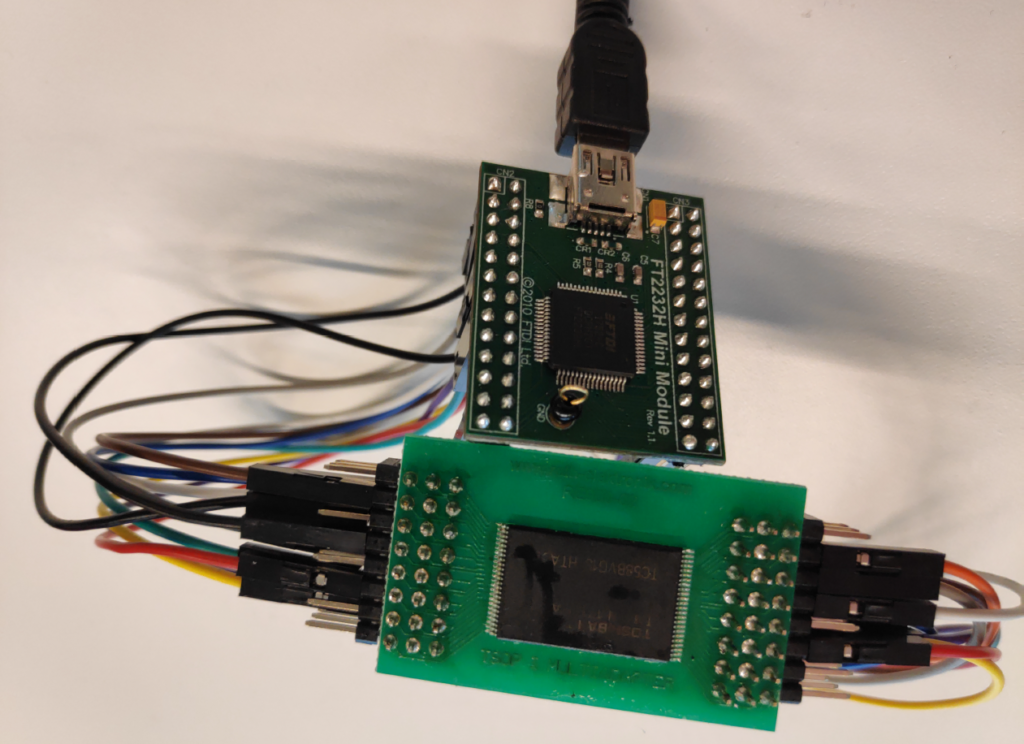
We successfully dumped the contents of the NAND chip however since it was at the end of my research internship there was not enough time left to recover all data. Even without fully being able to reverse engineer the IP camera we were able to test or approximate adherence to the requirements of the ETSI standard by analysing the wireless traffic and reversing the smartphone application. We found that about 14 requirements of the ETSI provisions were not fulfilled by the IP camera.
Discussion
Besides finding out whether the IP camera adhered to the ETSI standard the research provided me with a lot of knowledge about the reverse engineering pro-cess of an IoT device. The difficulty and the time it takes to reverse engineer a IoT device was not apparent to me before as I had not attempted to reverse engineer a modern IoT device before. Through the research I have also gained insights on whether legislation is catching up on the advancements in technology and I have to say that the ETSI standard seems to me like a good start.
Links
[1] https://www.etsi.org/deliver/etsi_en/303600_303699/303645/02.01.00_30/en_ 303645v020100v.pdf
[2] https://owasp.org/www-pdf-archive/OWASP-IoT-Top-10-2018-final.pdf
[3] O. Shwartz, Y. Mathov, M. Bohadana, Y. Elovici, and Y. Oren. Reverse engineering iotde-
vices: Effective techniques and methods.IEEE Internet of Things Journal, 5(6):4965–4976,Dec 2018 https://doi.org/10.1109/JIOT.2018.2875240
[4] https://github.com/ohjeongwook/dumpflash
About the Partners

Radboud University
University
Radboud University is a public university with a strong focus on research located in Nijmegen, Netherlands

Secura
Cybersecurity
Secura is an independent, specialized security expert with offices in Eindhoven and Amsterdam


0 Comments